Cyber security: the perils of not acting on early warning signals
By Ian Mitroff and Natalia Smalyuk
Three quarters of cyber crises are the result of issues that are not dealt with on time. While this may sound shocking, there are signals one can watch out for warning an organization that potential trouble is on the horizon.
What are such signals?
The recent example of Colonial Pipeline is instructive. A small group of hackers launched a ransomware attack on the U.S.' largest pipeline network for delivery of refined petroleum products. The hack disrupted the fuel supply to the country’s entire southeast. It was launched by using just one stolen password. At the time of the attack, there was no multifactor authentication on Colonial’s VPN account. That’s an early warning signal, if not a strong indicator, that the entire system is vulnerable to a cyber event.
In crisis-prone organizations, ordinary risks have a tendency to escalate into adverse events that threaten their stakeholders, reputation and bottom line. What these companies have in common is allowing warning signals to slip under the radar. Not recognizing – and not acting on – red flags, such as bad actors, irregular behaviour, unplanned updates, and unauthorized configuration changes, these organizations let underlying issues incubate instead of dealing with them head-on in early detection and mitigation programs. Unfortunately, cyberattacks can go on unnoticed for a very long time. And the longer they remain unnoticed, the more havoc they can wreak.
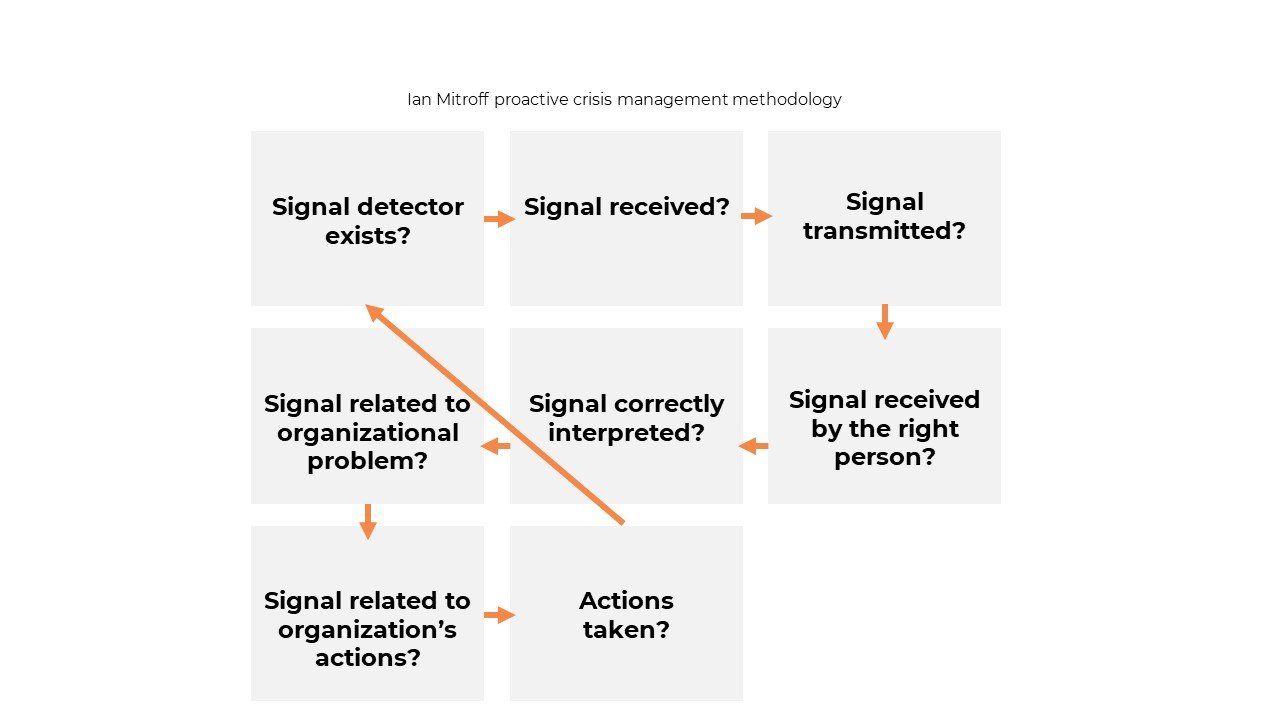
To prevent or mitigate the damage of these “predictable surprises,” organizations need to make every effort to pick up on early warnings, such as weak passwords or high click rates on their employee phishing tests. Just as importantly, they must act. The chart below shows the steps signals need to surmount in order to be fully addressed.
We urge leaders to think about all the various signals indicating that their organizations may be a target of a cyberattack. To guide them, we’ve put together some examples below. They’re organized into internal and external quadrants. These signals include both the technology and the people side of cyber security. This classification of signals is based on Mitroff’s proactive crisis management methodology.
Internal Signals
External Signals
If you’re interested in a further discussion of signal detection or want to gain a deeper understanding of your organization’s vulnerabilities, email us at nsmalyuk@nbau.ca and ian@mitroff.net. We look forward to speaking with you!